My Raspberry Pi is setup as a home server, providing me access and control of my content through several services:
- A Deluge server for torrent downloads.
- A Plex server to manage and stream my media collection.
- A Pydio server for remote access and management of files.
This is great, but I want to access my content when I’m away from home. Previous experience with remote access solutions inspired some requirements:
- I should be able to access my services from any computer in the world.
- I should be able to punch in an easy to remember web address like deluge.crawford.kiwi. This means all standard HTTP/HTTPS ports should be used!
- All transmission of my content should be encrypted.
- Moving house or ISP shouldn’t break my remote access.
Problems with home internet connections

The hardest requirement to cater to is that moving house or ISP shouldn’t break my remote access. Why is this such an issue?
May not have a static IP
Very rarely does a home connection come with a static IP. Getting a static IP typically results in extra charges, and would require updating the DNS record if anything changes. The solution is to use a dynamic DNS service which solves both these issues, but we still end up with the below problems.
May not have control of the router
Port forwarding needs to be setup on your router so incoming connections are forwarded to the home server. However, you may not have full control over the router to setup these rules. Many routers will also take the default HTTP/HTTPS ports for their own services, leaving you with non-standard port numbers for everything else.
May not be able to get incoming connections
Finally, once we’ve sorted out everything above, you may not be able to get incoming traffic to reach your house! As a result of the IPv4 address shortage and ISP firewalls, incoming connections don’t always work. Never fear, we can still tunnel traffic through the internet with the help of another computer with a more accessible connection.
Tunnelling out
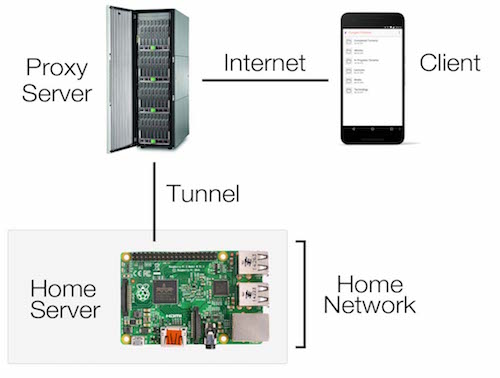
The concept of using a tunnel is pretty simple. We may not be able to get incoming connections to the home server, but the home server can setup an outgoing tunnel connection with some other machine on the internet. This other machine can be accessed from anywhere and forward connections through the tunnel to get to the home server.
The Other Machine
To meet my crazy requirements above, some other machine needs to be involved. There are services dedicated to providing remote access to your networks like Hamachi. These work well but require client software to join the virtual network, not meeting my first requirement of working on any computer!
Other than that, there are virtual private network (VPN) services which provide port forwarding, however it’s unlikely you’d be able to use the HTTP and HTTPS ports.
Last resort, DIY! A virtual private server (VPS) is a cheap way to get a small cloud server with a decant connection and its very own IPv4 address! For this I grabbed a VPS server from Vultr, whose cheapest server has more than enough grunt to provide remote access.
Reverse SSH Tunnel
A common way to get remote access through a firewall is with a Reverse SSH Tunnel. This is easy to setup and works well, but I discovered that HTTP based services through the tunnel run extremely slow. The most likely reason for this is that both SSH and HTTP use the TCP protocol to transmit data over a network. TCP ensures a reliable connection with built-in error checking and transmission control but this comes at a cost of speed. Running HTTP through the SSH tunnel is performing these error checks twice, resulting in much slower speeds.
The answer is to switch to something UDP based. UDP is much faster because it’s just packets sent straight over the network without error checking or flow control. A UDP based tunnelling solution means that only the HTTP layer is performing these extra tasks.
tinc VPN
The tinc VPN software was the answer. tinc can be used to create virtual networks between computers. It utilises UDP so runs quickly, all traffic is encrypted, and it’s continually re-checking the status of its VPN connection so works well even on unreliable connections.
I posted an article about how to configure tinc for this purpose, but this DigitalOcean tutorial is good resource too. This involves setting up the network’s configuration, generating key-pairs and copying the key-pairs between the machine.
To get tinc running I used jenserat’s tinc for the cloud server for my server and created a Docker image of my own for my Raspberry Pi (source code). However as of 2024 the jenserat image is very out of date and I’ve deleted my image from Docker Hub as it was out of date and insecure. I’d recommend installing the package manually or finding a Docker image which is more regularly updated.
Pretty URL’s
Proxying Connections
With tinc working, all the services on the home server can be accessed through a local IP on the cloud server, like 10.0.0.2:8112 for Deluge. Time to turn that into something nice like deluge.crawford.kiwi!
The subdomains point to the cloud server’s IP address. The cloud server has a NGINX server running with the official NGINX Docker image. NGINX is setup as a proxy server to the home server’s IP address using the NGINX documentation, meaning external traffic is forwarded through the tinc link to the home server.
HTTPS

HTTPS is used to ensure all data transport is encrypted. This requires valid SSL certificates which can be obtained for free with Let’s Encrypt through their automated verification process. To setup Let’s Encrypt to automatically renew I used bringnow’s docker-letsencrypt-manager and shared the volumes with the NGINX container. A very useful tool when working with HTTPS is SSL Labs’ SSL Test.
Using Plex
Plex is a powerful media server, allowing access to your media from anywhere. Plex offers Relay, a feature that allows tunnelling into your home server in a similar way to my setup. This works well, but does have bandwidth limitations. To setup MyPlex through the tinc tunnel I used this Gist to help with the NGINX configuration, and setup a custom URL in my Plex settings, like: https://plex.crawford.kiwi:443 (the port number must be explicitly defined for it to work). This works well, but I did have difficulties when Chromecasting from Android while on an external network, hopefully Plex will release a fix for this.
If you need some help crafting your NGINX configuration, checkout my NGINX example configuration on GitHub.
Take Away
While my original requirements were pretty over the top, I’m happy I have a solution which satisfies them. I have been using this setup reliably for about three months and having an easy to remember web address for all my home services is great. This process has taught me a lot about Docker, NGINX, and networking, much of which has already become useful in other contexts.
Edit, 29 Oct 2017: Added a link to my new tinc setup guide.
Edit, 13 Jan 2020: Added a link to my new NGINX configuration example.
Edit, 13 Oct 2024: I have removed a dead link to a Raspberry Pi tinc Docker image I made. This image was very out of date so were a security risk. As I am no longer in a position to maintain this image so I have deleted these images and make more up to date recommendations here.
